Part 2: Building Resilience - Continuous Hardening in OT/ICS Cybersecurity
Cybersecurity Awareness Month Blog Series: Part 2
In today’s interconnected industrial landscape, the convergence of Information Technology (IT) and Operational Technology (OT) has revolutionized efficiency, productivity, and automation. However, this integration has also expanded the attack surface, introducing complex cybersecurity challenges. As we continue our Cybersecurity Awareness Month series, we’ll explore how continuous hardening practices can help organizations mitigate these challenges and strengthen the resilience of their OT environments.
Understanding Operational Technology and Its Importance
Operational Technology refers to the hardware and software systems used to monitor and control physical processes, devices, and infrastructure in industrial environments. These systems are critical to industries such as manufacturing, energy, transportation, and utilities. Unlike IT systems, which prioritize data processing and storage, OT environments focus on safety, reliability, and real-time operations. A disruption or compromise in OT systems can lead to severe consequences, including safety hazards, production downtime, and financial losses.
The Cybersecurity Landscape in OT Environments
The increasing digitization and connectivity of OT systems have made them attractive targets for cybercriminals. Many OT environments still rely on legacy systems, proprietary protocols, and minimal security measures, leaving them vulnerable to threats such as ransomware, malware, and insider attacks. Furthermore, the interdependence between IT and OT systems means that a breach in one domain can have cascading effects on the other, amplifying the risk.
What is Continuous Hardening?
Continuous hardening is a proactive, ongoing approach to improving the security posture of OT environments. Unlike traditional, one-time security measures, continuous hardening evolves alongside the threat landscape. It involves regularly assessing, configuring, and enhancing security controls to reduce vulnerabilities and safeguard against emerging threats. This iterative process ensures that OT systems remain resilient in the face of ever-changing cyber risks.
Key Components of Continuous Hardening in OT
To implement continuous hardening effectively, organizations should focus on the following key components:
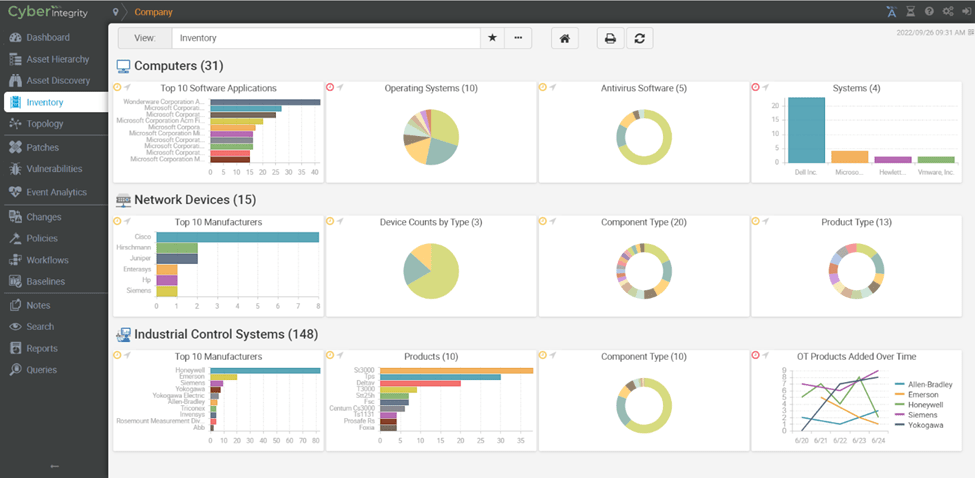
1. Asset Inventory and Management
Maintaining an accurate and up-to-date inventory of all OT assets is foundational to security. This involves identifying, categorizing, and documenting all devices, systems, and software within the OT environment. A comprehensive inventory helps organizations prioritize security measures, detect unauthorized devices, and respond quickly to potential threats.
2. Vulnerability Management
Regular vulnerability scanning and prompt patching or mitigation are essential for reducing risk. However, given the critical nature of OT systems, patch management must be carefully planned to avoid operational disruptions. A risk-based approach—prioritizing vulnerabilities that pose the greatest threat—ensures that resources are allocated effectively.
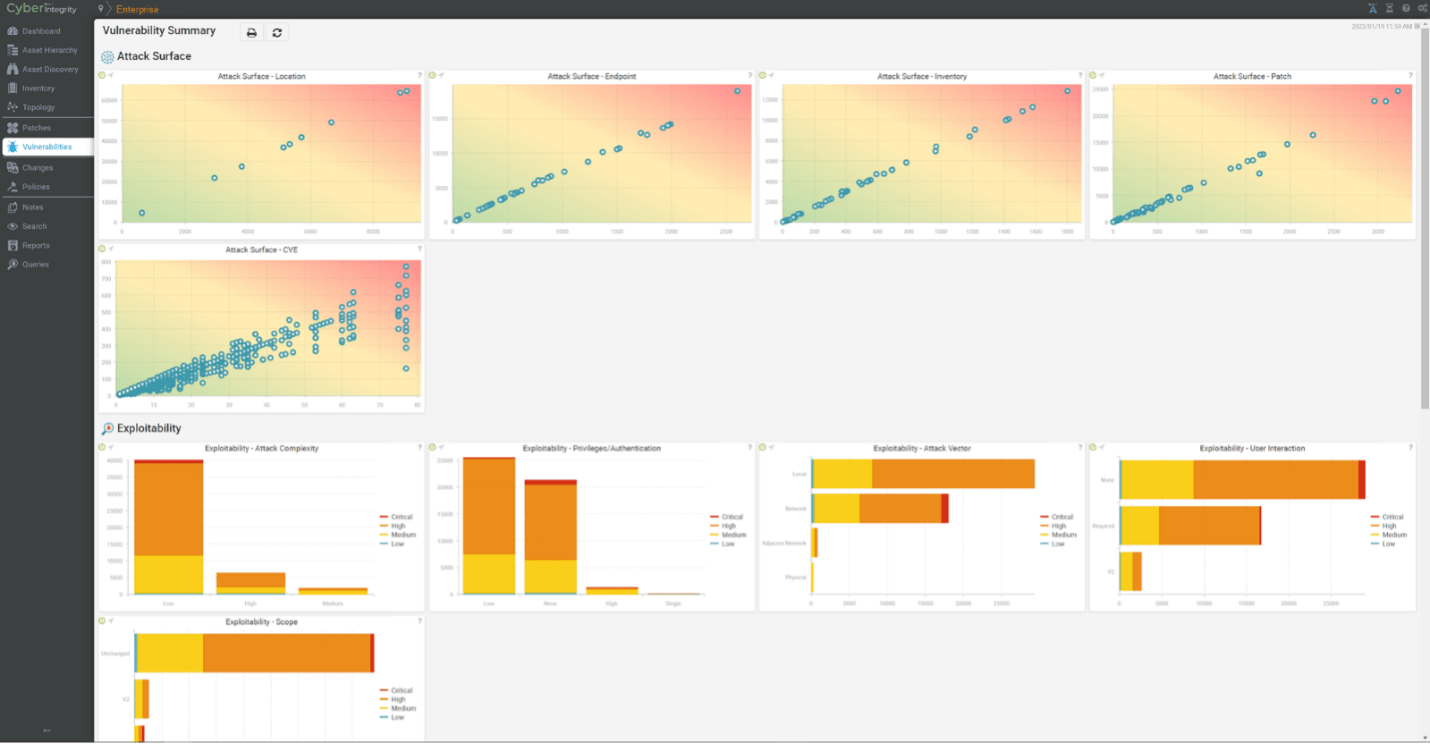
3. Network Segmentation
Network segmentation is a powerful strategy for limiting the spread of malware and restricting unauthorized access. By dividing the OT network into isolated zones, organizations can control and monitor traffic flow, reducing the risk of lateral movement by attackers. This segmentation is especially important in safeguarding critical assets and systems from potential breaches.
4. Access Control and Authentication
Enforcing strict access controls and multi-factor authentication (MFA) is crucial for preventing unauthorized access to OT systems. Role-based access control (RBAC) ensures that users have only the minimum privileges required to perform their tasks, thereby reducing the risk of insider threats or accidental misuse.
5. Continuous Monitoring and Incident Response
Real-time monitoring solutions, such as Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) tools, enable organizations to detect anomalies and potential threats as they occur. A well-defined incident response plan ensures that security teams can respond quickly and effectively to mitigate damage and restore normal operations.
6. Security Awareness and Training
Human error remains one of the most significant vulnerabilities in OT environments. Regular training and awareness programs empower employees to recognize and avoid social engineering attacks, phishing attempts, and other human-targeted threats. Cultivating a culture of security awareness ensures that every team member plays a role in protecting the organization.
Benefits of Continuous Hardening
- Enhanced Resilience: Continuous hardening reduces vulnerabilities, making OT systems more resistant to cyber threats.
- Minimized Downtime: Proactive measures help prevent disruptions, ensuring the availability and reliability of critical systems.
- Regulatory Compliance: Regular hardening practices help organizations meet cybersecurity standards and regulatory requirements.
- Cost Savings: Preventing incidents is far less costly than recovering from a breach or operational disruption.
Continuous hardening is a vital strategy for safeguarding OT environments against the evolving cyber threat landscape. By adopting a proactive and iterative approach to security, organizations can enhance the resilience, reliability, and safety of their industrial systems. As the convergence of IT and OT continues to drive innovation, it also necessitates a more vigilant approach to cybersecurity.
Investing in continuous hardening not only protects against cyber threats but also ensures the uninterrupted operation of critical industrial processes. This approach fosters a culture of preparedness, empowering organizations to adapt to emerging risks while maintaining compliance with regulatory requirements. In an era where cyberattacks can have devastating consequences, continuous hardening stands as a cornerstone of modern OT cybersecurity strategy—protecting not only the systems themselves but also the people, communities, and industries that depend on them.
As we move forward in this series, we’ll explore additional strategies to enhance OT security, including advanced threat detection, incident response planning, and the role of emerging technologies in safeguarding industrial environments. If you missed Part 1 of the series, you can read it here.
